Schneider Electric Hit by Hellcat Ransomware Attack: Major Data Breach Highlights Energy Sector Vulnerabilities
Nov 8, 2024
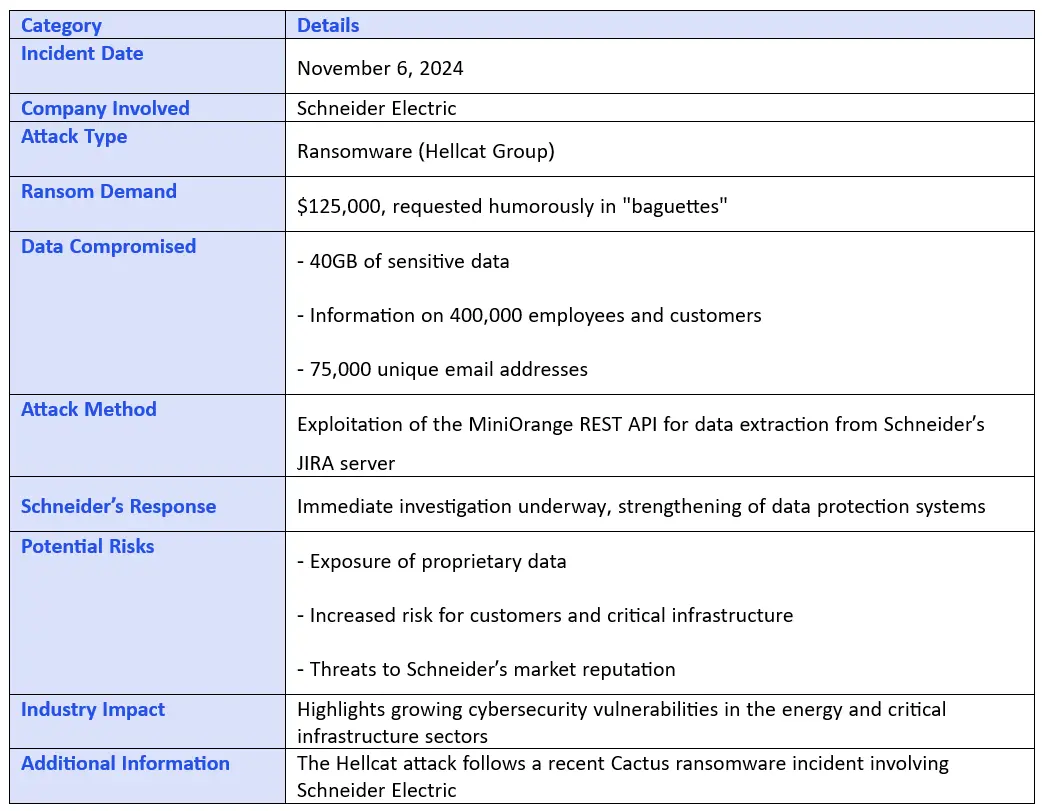
In a cybersecurity incident impacting Schneider Electric, a prominent French manufacturer in the energy sector, the Hellcat ransomware group claimed responsibility for a recent data breach. The group reportedly accessed 40GB of sensitive data, targeting Schneider's developer platform, and demanded a $125,000 ransom, humorously requested as payment in "baguettes."
Breach Details:
Scope of Data Compromised: The Hellcat group accessed Schneider’s JIRA server, reportedly scraping sensitive information on 400,000 employees and customers. This includes approximately 75,000 unique email addresses alongside names, escalating concerns about user data security and corporate espionage within the critical infrastructure sector.
Methods of Attack: According to Hellcat, the breach was facilitated using the MiniOrange REST API, a tool that allowed extensive data extraction. This breach is the second major incident Schneider Electric has faced in recent months, following an earlier Cactus ransomware attack.
Implications:
Impact on Schneider Electric: As a leader in industrial control systems, Schneider’s compromised data could weaken its market reputation and expose its infrastructure to additional risks. Given the critical nature of Schneider’s services, any vulnerabilities may have far-reaching implications for both the energy and industrial sectors.
Potential Risks to Customers: With Schneider’s widespread influence in energy management, this breach raises serious concerns about data security for clients and partners, potentially endangering both enterprise and critical infrastructure operations globally.
Response and Security Measures:
Schneider’s Actions: Schneider Electric acknowledged the breach within the demanded 48-hour timeframe, indicating an active investigation and efforts to fortify its data protection systems to deter future incidents.
Industry Reflection: This breach underscores the ongoing vulnerability of the energy sector to ransomware attacks. Companies managing critical infrastructure may face increasing pressure to adopt enhanced cybersecurity frameworks, from encrypted data storage to regular security audits.
This breach by Hellcat reveals the rising sophistication of ransomware groups and their unconventional ransom demands. As cybersecurity threats continue to evolve, industry leaders are urged to reinforce their security practices to guard against data compromises.
Disclaimer: ClearPhish maintains a strict policy of not participating in the theft, distribution, or handling of stolen data or files. The platform does not engage in exfiltration, downloading, hosting, or reposting any illegally obtained information. Any responsibility or legal inquiries regarding the data should be directed solely at the responsible cybercriminals or attackers, as ClearPhish is not involved in these activities. We encourage parties affected by any breach to seek resolution through legal channels directly with the attackers responsible for such incidents.