Critical Citrix NetScaler Vulnerabilities Exploited: How to Protect Your Systems from Brute-Force Attacks
Dec 13, 2024
A sharp increase in cyberattacks targeting Citrix NetScaler devices has been reported, with attackers exploiting misconfigured systems and leveraging recent vulnerabilities. These attacks, originating predominantly from a Hong Kong-based cloud provider, coincide with critical vulnerabilities CVE-2024-8534 and CVE-2024-8535 disclosed in November 2024.
The ongoing campaign highlights the pressing need for organizations to address these vulnerabilities to prevent severe breaches.
The Threat Landscape
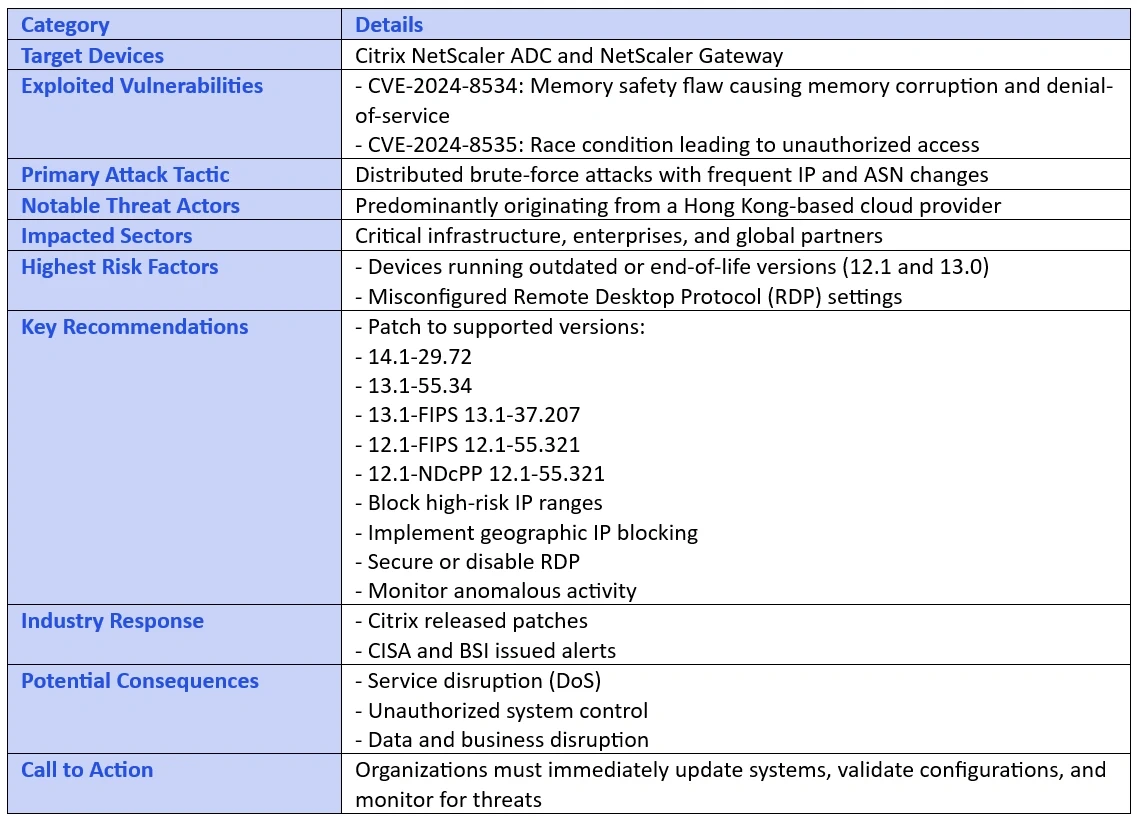
Citrix NetScaler devices, widely used in enterprise environments for application delivery and security, are currently in the crosshairs of attackers. Cybercriminals are employing distributed brute-force attacks, frequently rotating IP addresses and Autonomous System Numbers (ASNs) to evade detection.
The vulnerabilities being exploited include:
CVE-2024-8534: A memory safety flaw leading to memory corruption and potential denial-of-service attacks.
CVE-2024-8535: A race condition vulnerability that allows authenticated users to gain unauthorized capabilities.
Ethan Fite, Director of Managed Services Operations at Cyderes, noted the sophisticated tactics used by attackers. “Their distributed brute-force strategy and frequent IP changes create a challenging environment for security teams,” Fite said.
The German Federal Office for Information Security (BSI) has also raised alarms, citing multiple reports of attacks on critical infrastructure sectors across international partners.
Impact and Risks
Unpatched and outdated Citrix NetScaler devices are at the highest risk, particularly versions 12.1 and 13.0, which have reached end-of-life and no longer receive security updates. Exploiting these vulnerabilities could allow attackers to:
Compromise system integrity.
Escalate privileges or bypass authentication.
Disrupt services through denial-of-service attacks.
Given the widespread deployment of NetScaler in critical sectors, the consequences of these breaches could be severe, affecting business continuity and data security.
Recommended Mitigation Steps
Experts strongly recommend that organizations using Citrix NetScaler devices take immediate action:
Patch Vulnerable Systems: Apply security updates released by Citrix addressing CVE-2024-8534 and CVE-2024-8535. Ensure devices are upgraded to the latest supported versions:
14.1-29.72
13.1-55.34
13.1-FIPS 13.1-37.207
12.1-FIPS 12.1-55.321
12.1-NDcPP 12.1-55.321
Devices running versions 12.1 and 13.0 should be decommissioned or replaced.
Restrict Access:
Block high-risk IP ranges, especially those linked to the Hong Kong-based cloud provider.
Implement geographic IP blocking where operationally feasible.
Secure RDP Configurations:
Ensure the Remote Desktop Protocol (RDP) is securely configured or disable it if unnecessary.
Monitor for Anomalous Activity:
Watch for spikes in failed login attempts or unusual traffic patterns.
Validate Device Configurations:
Regularly audit and validate the security settings of NetScaler devices.
Global Response
Citrix has been proactive in addressing the issue by releasing patches for supported devices. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also issued an alert, warning organizations of the potential for complete system compromise if the vulnerabilities are exploited.
Security researchers and international agencies continue to monitor the situation closely, emphasizing the importance of proactive defense in mitigating these threats.
Looking Ahead
The spike in attacks on Citrix NetScaler devices underscores a broader trend: cybercriminals increasingly exploit zero-day vulnerabilities and misconfigurations to target critical infrastructure. Organizations must remain vigilant, prioritize patch management, and adopt robust monitoring solutions to safeguard against these evolving threats.
Disclaimer: ClearPhish maintains a strict policy of not participating in the theft, distribution, or handling of stolen data or files. The platform does not engage in exfiltration, downloading, hosting, or reposting any illegally obtained information. Any responsibility or legal inquiries regarding the data should be directed solely at the responsible cybercriminals or attackers, as ClearPhish is not involved in these activities. We encourage parties affected by any breach to seek resolution through legal channels directly with the attackers responsible for such incidents.