Clop Ransomware Exploits Cleo Vulnerabilities: Data Theft and Security Risks Unveiled
Dec 17, 2024
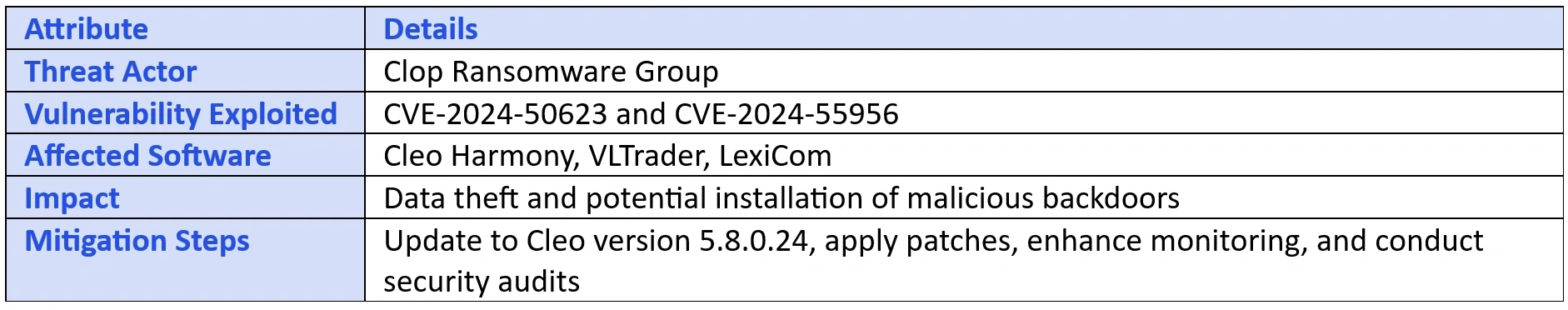
The notorious Clop ransomware gang has claimed responsibility for recent attacks exploiting vulnerabilities in Cleo's file transfer platforms, compromising critical corporate networks and exfiltrating sensitive data.
Exploiting Zero-Day Vulnerabilities
Cleo, a leading provider of managed file transfer software such as Cleo Harmony, VLTrader, and LexiCom, was targeted using two significant zero-day vulnerabilities: CVE-2024-50623 and CVE-2024-55956.
CVE-2024-50623, disclosed in October, allowed unrestricted file uploads and remote code execution. While Cleo patched this issue in version 5.8.0.21, researchers discovered the fix was incomplete.
The CVE-2024-55956 vulnerability emerged in December, permitting attackers to exploit Cleo platforms again for arbitrary file writes and JAVA backdoor uploads.
Cybersecurity researchers, including Huntress, confirmed that the flaws enabled attackers to install malicious backdoors like "Malichus," facilitating data theft, remote command execution, and deeper network access.
Clop's Admission of Responsibility
Initially attributed to a new ransomware group named "Termite," the attacks bore hallmarks of Clop's operations. Clop confirmed that they orchestrated both exploits, including the exploitation of Cleo's vulnerabilities:
"As for CLEO, it was our project (including the previous CLEO) - which was successfully completed," Clop stated.
Clop added that they typically avoid exposing sensitive data tied to government services, healthcare, and institutions, pledging to delete such data without hesitation.
Widespread Implications
The attacks on Cleo's platforms highlight ongoing risks associated with file transfer software vulnerabilities. Organizations using Cleo Harmony, VLTrader, or LexiCom are urged to apply the latest updates (5.8.0.24) immediately to mitigate exploitation risks.
Cybersecurity experts recommend proactive vulnerability management, enhanced monitoring, and immediate patch deployment to defend against ransomware attacks targeting critical infrastructure.
Final Thoughts
The Clop ransomware gang’s successful exploitation of Cleo systems underscores the importance of swift vulnerability remediation and robust cybersecurity protocols. Organizations must remain vigilant as ransomware groups continue to evolve their tactics and exploit zero-day vulnerabilities to compromise sensitive networks.
Disclaimer: ClearPhish maintains a strict policy of not participating in the theft, distribution, or handling of stolen data or files. The platform does not engage in exfiltration, downloading, hosting, or reposting any illegally obtained information. Any responsibility or legal inquiries regarding the data should be directed solely at the responsible cybercriminals or attackers, as ClearPhish is not involved in these activities. We encourage parties affected by any breach to seek resolution through legal channels directly with the attackers responsible for such incidents.