Cyberattack Hits Japan Airlines: Flight Delays Disrupt Holiday Travel Plans
Dec 27, 2024
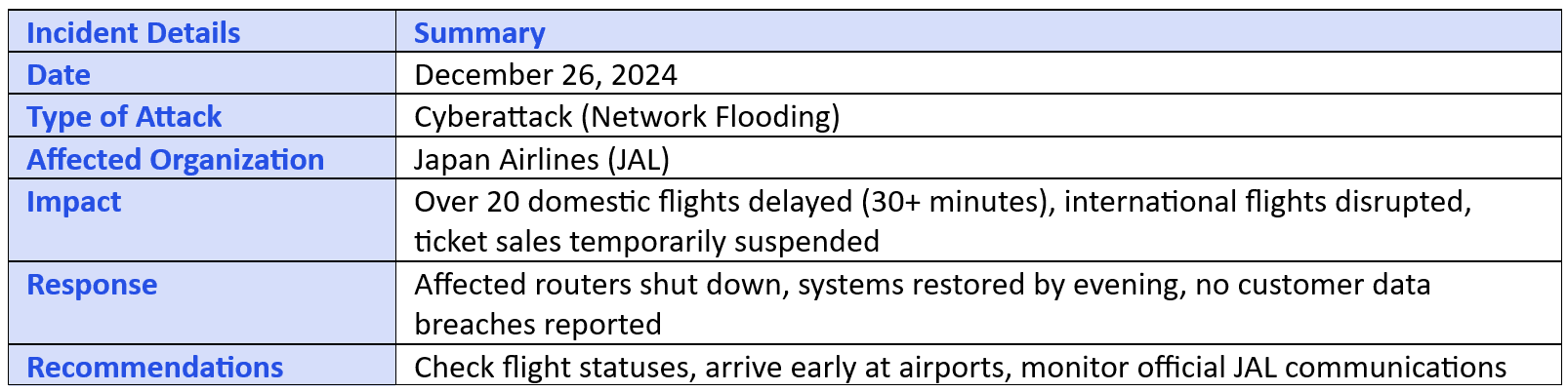
On December 26, 2024, Japan Airlines (JAL) experienced a cyberattack that disrupted both domestic and international flights during the busy year-end holiday season.
Incident Overview
The attack began at 7:24 a.m., targeting JAL's internal and external network systems. This led to malfunctions in systems that communicate with external platforms, causing delays and the temporary suspension of same-day ticket sales.
Impact on Flights
The cyberattack resulted in delays for more than 20 domestic flights, each exceeding 30 minutes. International flights also faced disruptions, though specific details were not disclosed. The timing of the attack coincided with Japan's peak travel period, intensifying its impact on passengers.
Response and Recovery
JAL promptly identified the issue as a data flood intended to overwhelm their network. By temporarily shutting down affected routers and suspending ticket sales, the airline managed to restore systems by the evening of December 26. No customer data breaches or virus-related damages were reported.
Recommendations for Passengers
Passengers are advised to:
Check flight statuses regularly
Arrive at airports earlier than usual
Stay alert for official communications from JAL
Conclusion
This incident highlights the vulnerabilities in aviation cybersecurity, especially during high-traffic periods. It underscores the necessity for robust cyber defenses to protect critical infrastructure and ensure passenger safety.
Disclaimer: ClearPhish maintains a strict policy of not participating in the theft, distribution, or handling of stolen data or files. The platform does not engage in exfiltration, downloading, hosting, or reposting any illegally obtained information. Any responsibility or legal inquiries regarding the data should be directed solely at the responsible cybercriminals or attackers, as ClearPhish is not involved in these activities. We encourage parties affected by any breach to seek resolution through legal channels directly with the attackers responsible for such incidents.