Microsoft 365 Outage: Exchange, Teams, and SharePoint Disrupted - Root Cause and Recovery Updates
Nov 26, 2024
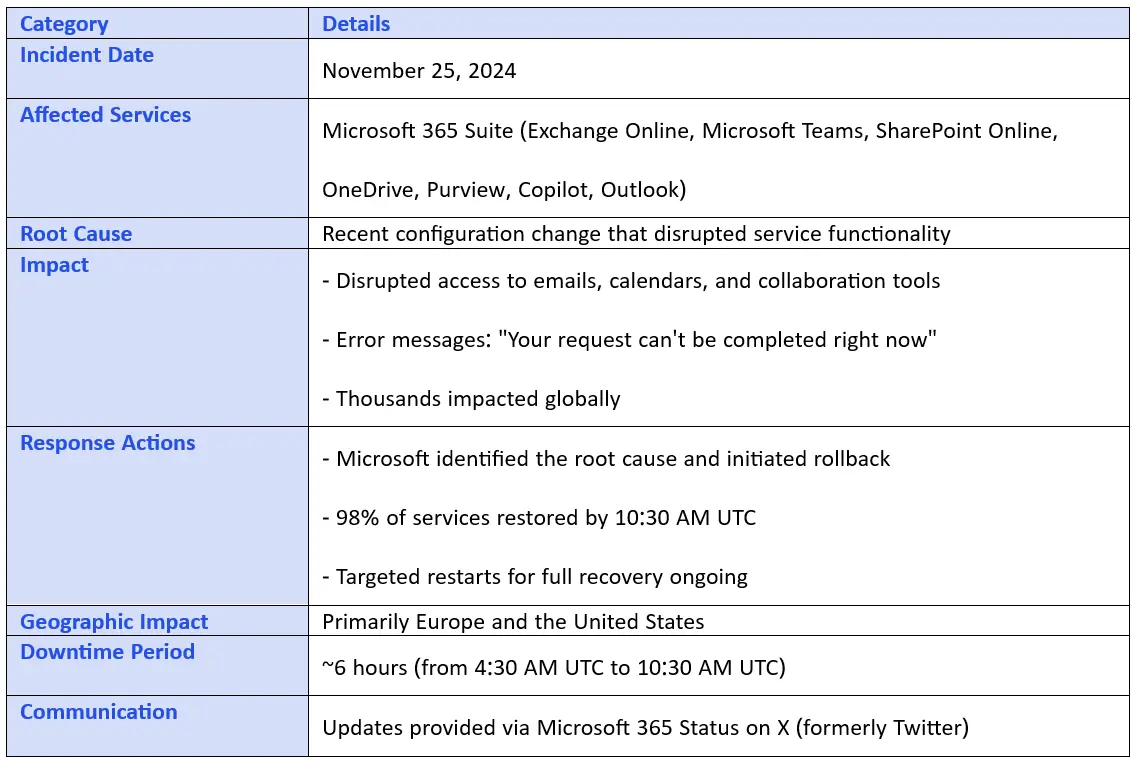
On November 25, 2024, Microsoft experienced a significant outage affecting multiple Microsoft 365 services, including Exchange Online, Microsoft Teams, and SharePoint Online. The disruption began around 4:30 AM UTC and persisted for several hours, impacting users' ability to access emails, calendars, and collaborative tools.
Incident Overview
Users reported difficulties accessing Exchange Online via Outlook on the web, desktop clients, and mobile devices. Additionally, functionalities within Microsoft Teams, such as calendar access, were disrupted. Other services, including OneDrive, Purview, Copilot, and Outlook, also issues.
Root Cause Analysis
Microsoft identified a recent configuration change as the root cause of the outage. The company promptly initiated a rollback of the change to mitigate the impact. By approximately 10:30 AM UTC, Microsoft reported that 98% of affected environments had been restored. However, some users continued to experience delays in recovery efforts.
User Impact
The outage affected thousands of users globally, with significant reports from Europe and the United States. Users encountered error messages stating, "Your request can't be completed right now," when attempting to access Outlook and other services. Reports on Downdetector.co.uk peaked with over 800 incidents around 7:30 AM UTC.
Microsoft's Response
Microsoft acknowledged the issue promptly and communicated updates through their Microsoft 365 Status account on X (formerly Twitter). The company expressed understanding of the significant impact on businesses and committed to providing relief as swiftly as possible. They also noted that targeted restarts were progressing slower than anticipated for the majority of affected users.
Conclusion
The November 25, 2024, Microsoft 365 outage underscores the critical importance of robust change management and rapid response strategies in cloud service operations. While Microsoft acted swiftly to identify and address the issue, the incident highlights the potential widespread impact of service disruptions on global business operations.
Disclaimer: ClearPhish maintains a strict policy of not participating in the theft, distribution, or handling of stolen data or files. The platform does not engage in exfiltration, downloading, hosting, or reposting any illegally obtained information. Any responsibility or legal inquiries regarding the data should be directed solely at the responsible cybercriminals or attackers, as ClearPhish is not involved in these activities. We encourage parties affected by any breach to seek resolution through legal channels directly with the attackers responsible for such incidents.