OnePoint Patient Care Data Breach Exposes Data of Nearly 800,000 Patients
Oct 28, 2024
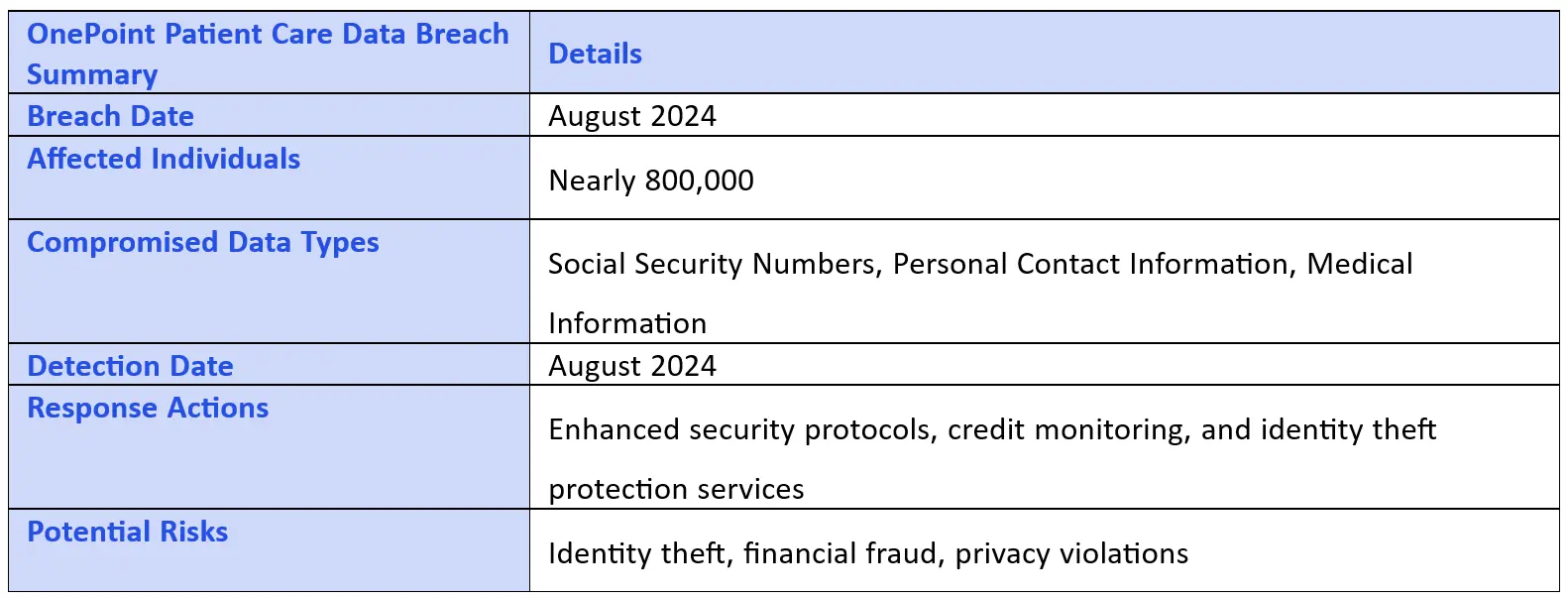
OnePoint Patient Care (OPPC), a well-known provider of pharmacy and hospice services, recently disclosed a significant data breach that has impacted the personal and medical information of nearly 800,000 individuals. The breach, which is one of the latest in a troubling series of healthcare-related data incidents, exposes individuals to substantial risk, highlighting ongoing vulnerabilities in the protection of sensitive healthcare data.
What Happened?
In August 2024, OnePoint Patient Care identified unusual activity within its network, triggering an internal investigation. Preliminary reports suggest that attackers gained unauthorized access to sensitive data held within OPPC's systems, exploiting security gaps to obtain patient information. Following the investigation, OPPC confirmed that the breach led to the exposure of highly confidential patient data. It is unclear at this time if the breach was part of a larger orchestrated attack or if it was targeted specifically at OPPC.
What Data Was Compromised?
OPPC has disclosed that the data accessed includes a range of sensitive information, making it a prime target for cybercriminals who may use this information for identity theft or financial fraud. The exposed data includes:
Social Security Numbers (SSNs): A critical element of personal identity, allowing cybercriminals to perpetrate identity theft.
Personal and Contact Information: Such as names, addresses, phone numbers, and dates of birth.
Medical Information: Including patient health records, diagnoses, and treatments.
The breach could have severe implications for affected individuals, given the nature and value of the compromised data in illicit markets.
Timeline of the Breach
OPPC has provided an initial timeline for the breach, outlining key events in the data incident:
Initial Suspicious Activity Detected (August 2024): Unusual network activity indicated a possible compromise.
Confirmation of Breach (September 2024): An investigation confirmed unauthorized access and data exposure.
Notifications Sent (October 2024): OPPC began notifying impacted individuals and took steps to secure its systems.
Potential Impact on Affected Individuals
For those impacted, the breach may have lasting consequences, including:
Financial Risk: Exposed SSNs and personal data could lead to unauthorized transactions and fraudulent activities.
Identity Theft: The compromised data offers cybercriminals a comprehensive identity package, increasing the risk of identity theft.
Privacy Concerns: Medical information exposure poses severe privacy concerns, potentially impacting individuals’ reputations and personal privacy.
OnePoint Patient Care’s Response
OnePoint Patient Care has stated they are working with cybersecurity professionals to address the breach and prevent similar incidents. The organization is implementing enhanced security measures and is offering credit monitoring and identity theft protection services to affected individuals.
Steps for Affected Individuals
If you believe you may be affected by this data breach, consider taking the following steps:
Monitor Your Credit: Check your credit reports for unusual activity and consider a credit freeze if necessary.
Utilize Offered Protection Services: Take advantage of the identity protection services offered by OPPC.
Stay Vigilant for Phishing Attacks: Be cautious of unsolicited communications requesting personal information.
Secure Online Accounts: Strengthen your account security by updating passwords and enabling two-factor authentication where possible.
This incident underscores the ongoing challenges in safeguarding healthcare data and highlights the critical need for robust cybersecurity measures in organizations managing sensitive personal information.
Disclaimer: ClearPhish maintains a strict policy of not participating in the theft, distribution, or handling of stolen data or files. The platform does not engage in exfiltration, downloading, hosting, or reposting any illegally obtained information. Any responsibility or legal inquiries regarding the data should be directed solely at the responsible cybercriminals or attackers, as ClearPhish is not involved in these activities. We encourage parties affected by any breach to seek resolution through legal channels directly with the attackers responsible for such incidents.